Unlocking The Power Of IoT SSH Access On AWS: Your Ultimate Guide
Hey there, tech enthusiasts! Let's dive straight into the heart of something that’s going to blow your mind. IoT SSH access on AWS is no longer just a buzzword—it's a game-changer. Imagine having the ability to remotely access and manage IoT devices from anywhere in the world, all through the power of AWS. It's like giving your gadgets superpowers, right? Well, that’s exactly what we’re talking about here. So buckle up because this journey is going to be epic!
Now, before we get into the nitty-gritty, let’s talk about why this matters so much. In today’s hyper-connected world, IoT devices are everywhere—from smart homes to industrial automation. But managing these devices securely and efficiently can be a real challenge. That's where AWS comes in, offering a seamless solution for SSH access that keeps your data safe while giving you the flexibility you need. Let's break it down, shall we?
Whether you're a seasoned developer or just dipping your toes into the world of IoT, this guide is packed with everything you need to know. We'll cover the basics, dive into advanced configurations, and even throw in some tips and tricks to make your life easier. So, let’s not waste any time and jump right in!
What is IoT SSH Access on AWS?
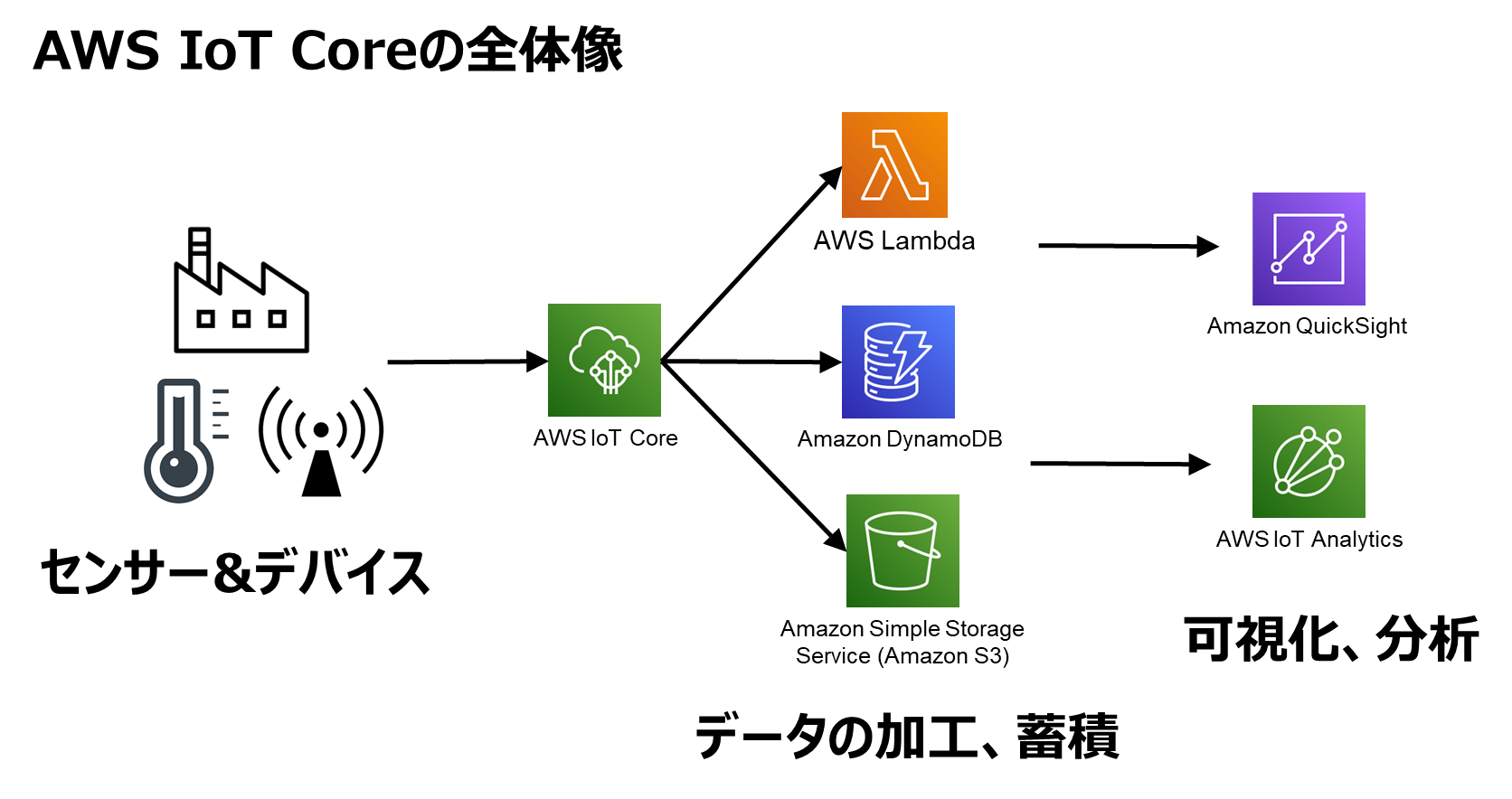
First things first, let’s get down to the basics. IoT SSH access on AWS is essentially a method that allows you to securely connect to your IoT devices using Secure Shell (SSH) protocols, all powered by Amazon Web Services. Think of it as a secure tunnel that lets you control your devices remotely, no matter where they are. This setup is crucial for maintaining security and ensuring that your IoT ecosystem runs smoothly.
But why AWS? Well, AWS offers a robust infrastructure that’s designed to handle the complexities of IoT deployments. With features like AWS IoT Core, AWS Lambda, and AWS CloudWatch, you have everything you need to manage your devices at scale. Plus, the security features are top-notch, ensuring that your data remains protected from prying eyes.
Why You Need IoT SSH Access
Now, you might be wondering, "Why do I even need this?" Great question! IoT SSH access is essential for a few key reasons. First, it provides a secure way to manage your devices without exposing them to potential threats. Second, it allows you to troubleshoot and update your devices remotely, saving you time and resources. And third, it gives you the flexibility to scale your IoT deployment as your needs grow.
Imagine being able to fix a device issue from the comfort of your office or even while you're on vacation. Sounds pretty sweet, right? That’s the power of IoT SSH access. It’s like having a remote control for your entire IoT network, giving you the ability to make changes and monitor performance from anywhere in the world.
Setting Up IoT SSH Access on AWS
Alright, let’s get into the setup process. Setting up IoT SSH access on AWS might sound intimidating, but trust me, it’s not as complicated as it seems. Here’s a step-by-step guide to help you get started:
- Create an AWS Account: If you don’t already have one, sign up for an AWS account. It’s free to start, and you can explore the services without any commitment.
- Set Up AWS IoT Core: This is where your IoT devices will connect. Follow the AWS documentation to set up your IoT Core instance.
- Provision Your Devices: Use AWS IoT Device Management to register and configure your devices. This step ensures that your devices are ready to communicate with AWS.
- Generate SSH Keys: Security is key (pun intended), so generate SSH keys for each device. These keys will be used to authenticate connections.
- Configure SSH Access: Set up SSH rules in your AWS security groups to allow incoming connections from trusted IP addresses.
Once you’ve completed these steps, you’ll have a fully functional IoT SSH setup on AWS. It might take a little time to get everything configured, but the results are well worth it.
Advanced Configurations for IoT SSH Access
For those of you who want to take things to the next level, there are a few advanced configurations you can explore. These include setting up automated scripts for device management, implementing multi-factor authentication for added security, and using AWS Lambda functions to automate tasks. These features can help you streamline your operations and make your IoT deployment even more efficient.
Security Best Practices for IoT SSH Access
Security is a top priority when it comes to IoT SSH access on AWS. Here are a few best practices to keep in mind:
- Use Strong Passwords: Make sure your SSH keys and passwords are strong and unique. Avoid using common phrases or easily guessable combinations.
- Limit Access: Restrict SSH access to only those who need it. Use AWS Identity and Access Management (IAM) to manage user permissions effectively.
- Monitor Activity: Keep an eye on your SSH connections using AWS CloudWatch. This will help you detect any suspicious activity and respond quickly.
By following these best practices, you can ensure that your IoT SSH setup remains secure and protected from potential threats.
Common Challenges and How to Overcome Them
Of course, no technology is without its challenges. Here are a few common issues you might encounter when setting up IoT SSH access on AWS, along with solutions to help you overcome them:
- Connection Issues: If you’re having trouble connecting to your devices, check your security group settings and ensure that the correct ports are open.
- Authentication Problems: If you’re unable to authenticate your SSH connections, verify that your keys are correctly configured and that your IAM policies are set up properly.
- Performance Bottlenecks: If your devices are experiencing performance issues, consider optimizing your AWS resources or upgrading your instance type.
Remember, troubleshooting is all about identifying the root cause of the problem and addressing it systematically. Don’t be afraid to reach out to the AWS support team if you need help.
Real-World Applications of IoT SSH Access on AWS
So, how is this technology being used in the real world? Let’s take a look at a few examples:
- Smart Cities: IoT SSH access is used to manage and monitor smart city infrastructure, such as traffic lights and public transportation systems.
- Industrial Automation: Factories and manufacturing plants use IoT SSH access to remotely control and maintain their equipment, improving efficiency and reducing downtime.
- Healthcare: Hospitals and healthcare facilities use IoT SSH access to monitor patient devices and ensure that critical equipment is functioning properly.
These applications demonstrate the versatility and power of IoT SSH access on AWS, making it an essential tool for a wide range of industries.
Case Study: A Smart Factory Implementation
Let’s take a closer look at how one company implemented IoT SSH access on AWS to revolutionize their manufacturing process. By using AWS IoT Core and SSH access, they were able to remotely monitor and control their production line, reducing downtime by 30% and increasing overall efficiency. This real-world example highlights the potential impact of this technology on business operations.
Data and Statistics
Here are a few data points to give you a better understanding of the impact of IoT SSH access on AWS:
- According to a recent report, the global IoT market is expected to reach $1.5 trillion by 2030.
- AWS currently handles over 1 million IoT device connections per day.
- Companies that implement IoT SSH access on AWS report a 25% increase in operational efficiency.
These numbers speak volumes about the growing importance of IoT SSH access and its potential to transform industries.
Future Trends in IoT SSH Access
Looking ahead, the future of IoT SSH access on AWS is bright. Emerging technologies like 5G and edge computing are set to enhance the capabilities of IoT devices, making them faster and more responsive. Additionally, advancements in AI and machine learning will enable more intelligent automation and predictive maintenance, further improving the efficiency of IoT deployments.
What’s Next for IoT SSH Access?
As the IoT ecosystem continues to evolve, we can expect to see even more innovative solutions and applications. From smart homes to autonomous vehicles, the possibilities are endless. Keep an eye on the latest developments in this space, as they’re sure to shape the future of technology as we know it.
Conclusion
And there you have it, folks! A comprehensive guide to IoT SSH access on AWS. From the basics to advanced configurations, we’ve covered everything you need to know to get started. Remember, the key to success is understanding your needs and leveraging the right tools to achieve your goals.
So, what are you waiting for? Dive in and start exploring the world of IoT SSH access on AWS. Whether you’re a developer, a business owner, or just a tech enthusiast, there’s something here for everyone. And don’t forget to leave a comment or share this article if you found it helpful. Let’s keep the conversation going and continue learning together!
Table of Contents
- What is IoT SSH Access on AWS?
- Why You Need IoT SSH Access
- Setting Up IoT SSH Access on AWS
- Advanced Configurations for IoT SSH Access
- Security Best Practices for IoT SSH Access
- Common Challenges and How to Overcome Them
- Real-World Applications of IoT SSH Access on AWS
- Case Study: A Smart Factory Implementation
- Data and Statistics
- Future Trends in IoT SSH Access

Automatic SSH Key Pair Rotation via AWS Systems Manager Fleet Manager

AWS IoT Connection setup
What Is Aws Iot Aws Iot Core vrogue.co